It is believed that the universe is made of atoms but given the digital wave orbiting our planet; one can vouch that the universe is made of data.
An integral asset, an uncompromised entity – Data Privacy would now garner more eyeballs than ever. As we dive deeper into the complexities revolved around it, let’s first understand data privacy in its entirety. Simply put, just like you rent lockers in banks to secure your valuables, data privacy allows you to lock your personal data. Data privacy enables you to protect your data by focusing on how to manage, store and share it with third parties thereby aligning with the laws and regulations of different countries and governing bodies.
What Makes Data Protection So Crucial
Needless to say that being part of a social community where sharing data is a common practice, safeguarding data gains utmost importance. While the responsible use of data can be a game-changer in driving brands, businesses, countries even. Its misuse, however, could lead to irreparable consequences and permanent damage to a brand’s goodwill. Data breaching, as is called, can hamper the secured information of an organization, government, and individual; by putting it for the wrong use. We all know that Data is sensitive yet 36 billion records were exposed owing to data breaches in just the first half of 2020. This has enabled many brands and platforms to consume data and ensure data security and privacy remain the utmost priority for the consumer.
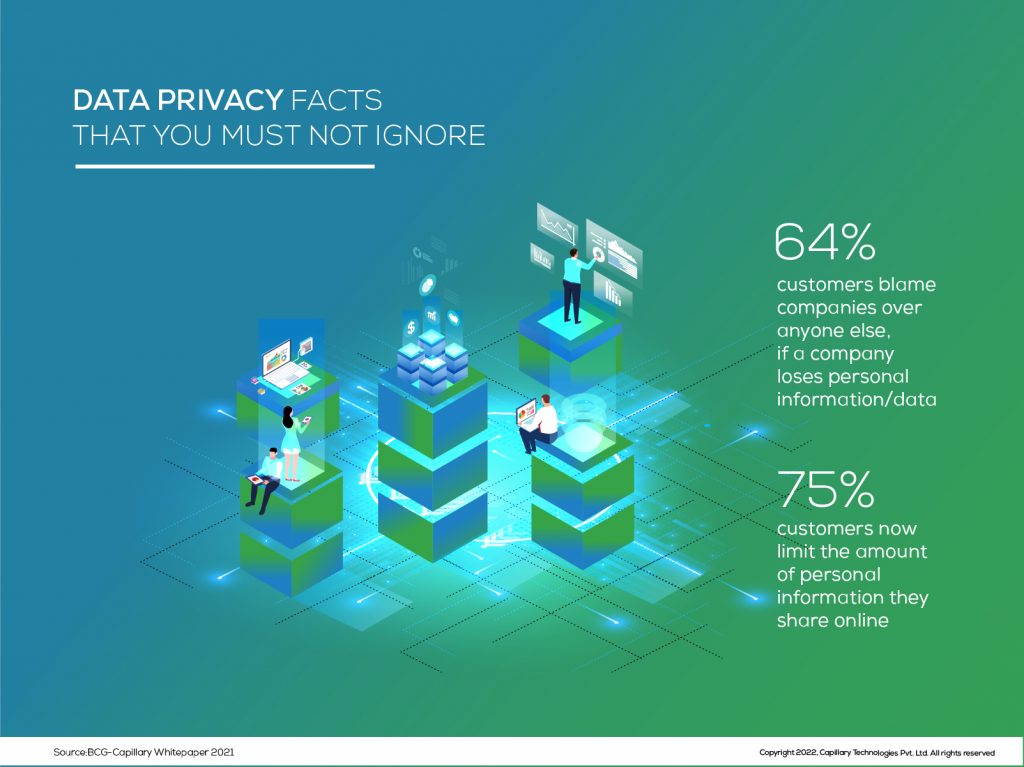
Going by the last two years’ facts and figures, when the digital footprint of mankind increased to its maximum, data is spreading far and wide. On an average day, we are exposed to so many adverts, e-mailers, and direct messages that we have lost count of the exact number. Data has become the quintessential commodity in every brand’s strategy. In fact, Capillary’s last webinar on the data-driven approach to customer engagement would have you center on one key question – We all know that data is the answer. But are customers willing to share it? If yes, how much data should ideally be shared? Before we proceed, here are some startling facts from the webinar to keep you hooked:
These statistics definitely echo people’s sentiments. There is no right answer to how much data we should share as that boils down to everyone’s own discretion. In a marketing arena where the customer is the king, their right to understand how their data is being utilized gains precedence. Given the norms, organizations now need to culturally change their pre-defined marketing practices and marketers must ensure transparency as part of their data strategies. But for marketers, there is definitely more to dive into when it comes to how to protect the data that enables strategic business decisions to drive brand revenue growth and overall goodwill. Thus, a marketer’s role in data privacy is more crucial because if they falter, they risk the brand image.
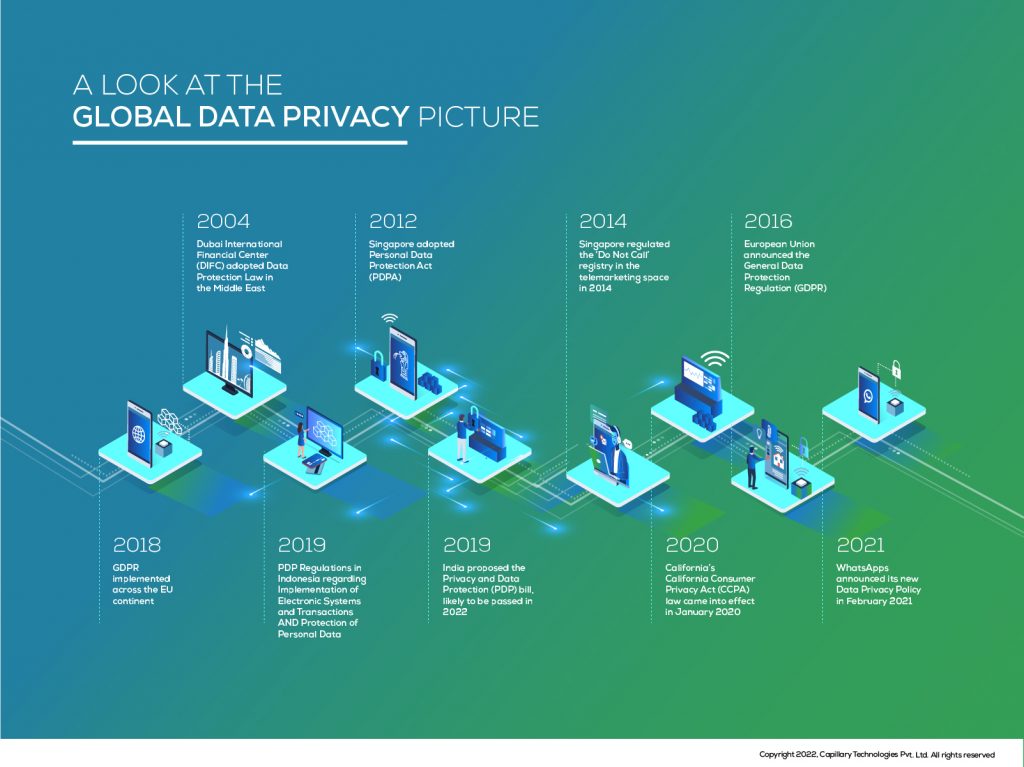
Data Privacy: A Look at the Global Picture
The above timeline illustrates the dire need to guard data – personal or professional with authentic norms. No wonder, it’s important for every individual, brand, organization to be compliant in this aspect. In fact, organizations that stay compliant with data protection have a competitive advantage over other players in the industry. For instance, when Apple Inc. stated that privacy is a human right, their customer advocacy swelled up. With the right set of data protection strategies in place, companies can gain the trust and advocacy of their customers, stakeholders, and clients.
Our Approach: Data Privacy at Capillary
At Capillary, our teams deal with innumerable large data sets for different clients. Data sets that are managed, distilled, and secured to derive high consumer engagement for our brands. For us, data security measures remain intact from day one. Data at rest is encrypted with state-of-the-art 128-256 bit keys. To credibly action our data protection strategy, we have a dedicated team headed by the Chief Information Security Officer (CISO) that consistently looks at the security element of the data. All production infrastructure is architected to sit within isolated Virtual Private Clouds (separate for computing, and storage). We adhere to a neat approach entailed below that allows us to be transparent to our clients.
1. Auditing
Capillary’s Information Security Management Forum (ISMF) performs Internal IS Audits on a periodic basis. Extensive audit logs are maintained for Capillary’s systems to investigate any suspected breaches, etc. assessing security controls, server provisioning, disaster recovery, and business continuity. Besides this, we also conduct consistent Audit Trails of all system actions that are readily available.
2. Client Assessment
At Capillary, we believe in customer transparency when any security vulnerabilities are discovered or reported. We use industry-standard bug bounty programs like SafeHats to engage with security researchers in a collaborative way. We have successfully undergone security assessments conducted by our clients including some of the leading global names across different industries.
3. Platforms
Our platforms are well-secured and follow the below practices to ensure data protection at all levels.
- Data Processing & Transfers: All the data transfers between client stores and warehouses and the cloud use secure FTP connections. When data is being transferred it can be in an encrypted format, if required. Larger data sets using raw files/flat files are transferred through a secured Capillary application.
- Role-based access control: The access control team provides the required level of access to the data for specific employees and clients. Access is immediately revoked when an employee’s record is terminated in Capillary’s HR system within 30 days.
- Reports: All client reports and dashboards are password encrypted and no raw data is sent with these reports. All members and Capillary employees have restricted access to the engagement they belong to. The access grants are reviewed every 90 days, and explicit pre-approval is required, failing which, access to the resource is revoked.
4. People
Two-factor authentication is used at all access points, including access to the development, pre-production, and production environments using dedicated VPN tunnels.
- Capillary access and administration of logical security rely on user IDs, passwords, and secure LDAP to authenticate users to services, resources, and devices as well as to authorize the appropriate level of access for the user.
- Capillary Security has established a password policy with required configurations and expiration intervals.
Our Certifications: Data Security at Capillary
We are certified by the ISO, PCI, compliant with SOC2, and GDPR compliant. This clearly highlights that with Capillary Technologies’ platform, there will be no security breaches and cyber-attacks as the architecture is strongly held. All this is to ensure clients’ data is guarded every time for their services.
And a case study about our data protection measures…
Capillary prides itself in following the data protection policies for all its clients to protect their consumer data. Our data security measures are widely known. In fact, Trend Micro, the multinational cyber security software company also elaborated on how Capillary Technologies optimizes security and visibility for its cloud platforms. You could read the detailed case study here.
People also ask ⁝
1.What are the key data privacy regulations businesses must comply with in the USA and Europe?
Businesses in the USA and Europe must comply with regulations such as GDPR in Europe and CCPA in California. Ensuring compliance with these laws protects consumer data and avoids hefty fines.
2.How can implementing robust data privacy practices improve customer trust for B2B companies?
Implementing robust data privacy practices helps B2B companies build trust with their clients by protecting sensitive information, leading to stronger business relationships and increased loyalty.
3.What are the best data privacy tools for Singapore and Hong Kong businesses?
In Singapore and Hong Kong, businesses can use tools like OneTrust, TrustArc, and BigID to manage data privacy, ensure compliance, and protect sensitive information.
4.Why is data privacy important for B2B transactions in the UAE and Saudi Arabia?
Data privacy is crucial for B2B transactions in the UAE and Saudi Arabia to safeguard confidential business information, maintain client trust, and comply with regional data protection laws.
5.How can data privacy impact B2B marketing strategies in India and Australia?
Data privacy impacts B2B marketing strategies by necessitating transparent data collection practices, obtaining explicit consent, and ensuring marketing efforts comply with regional data protection laws in India and Australia.